
How exposed is your company to cyber attacks?
Consult our security experts, identify your gaps and gain peace of mind

In addition to the growing number of cyber-attacks and the need to protect against them, the entry into force of the new Federal Data Protection Act (DPA) requires companies to have adequate data security in place. To find out whether your company is minimally protected against cyber-attacks and compliant with the DPA, here’s a list of questions to ask yourself:
- Do you have an IT security policy that enforces compliance with best practices and is well communicated within the organization?
- Are your procedures, management processes and IT infrastructure inventory well documented and regularly updated?
- Are your workstations, servers and applications adequately protected against threats?
- Do you have immutable and regularly tested backups for your critical IT assets?
- Do you have an incident response plan covering, among other things, cyber-attacks?
The IT security audit is an in-depth examination designed to assess your level of exposure to cyber-attacks and your level of compliance with legal requirements, such as the Data Protection Act (DPA), in terms of data security.
Why carry out an IT security audit?
Meanquest proposes three levels of intervention with offers perfectly adapted to the needs of SMEs of all sizes:
Have a security expert draw up an inventory of your organization’s compliance with the obligation to ensure data security, as required by the Data Protection Act.
Evaluate your level of IT security
Identify potential vulnerabilities and security holes in your IT systems
Submit pragmatic recommendations to achieve an acceptable level of risk for your sensitive and confidential data
Areas audited
Governance of
information
security
Information
System
Resources
humans
Steps in a security audit for information systems
Analysis and understanding of your organization's context
- Identification of your needs and expectations through management interviews
- Interviews with IT and HR infrastructure managers
Overview and analysis of IT security
- Analysis of the level of compliance and maturity of information security governance (roles and responsibilities, business continuity and recovery plan, etc.).
- Analysis of the level of cyber exposure linked to your information systems (management of IT assets, identifying flaws, weaknesses, vulnerabilities, access, malware, hackers, etc.).
- Analysis of HR management compliance and cyber exposure linked to human risk (recruitment, training & awareness, end of collaboration).
Audit report and recommendations for safety management
- Report including a risk analysis of cyber-attacks by malware, for example, and recommendations for dealing with the risks identified
- Presentation session of the draft IT security audit report
- Transmission of a final report via a secure platform
Confidentiality
The auditors undertake to treat all data, access, information and documents concerning the Company as confidential.
Further information about our audits
- Exclusions
- Document templates
- Correcting critical vulnerabilities and security flaws
- Implementation of a cybersecurity management system
- Possibility of correcting any security flaws detected (see service offering)
- Possibility of combining IT security audit with penetration testing
A scalable offering
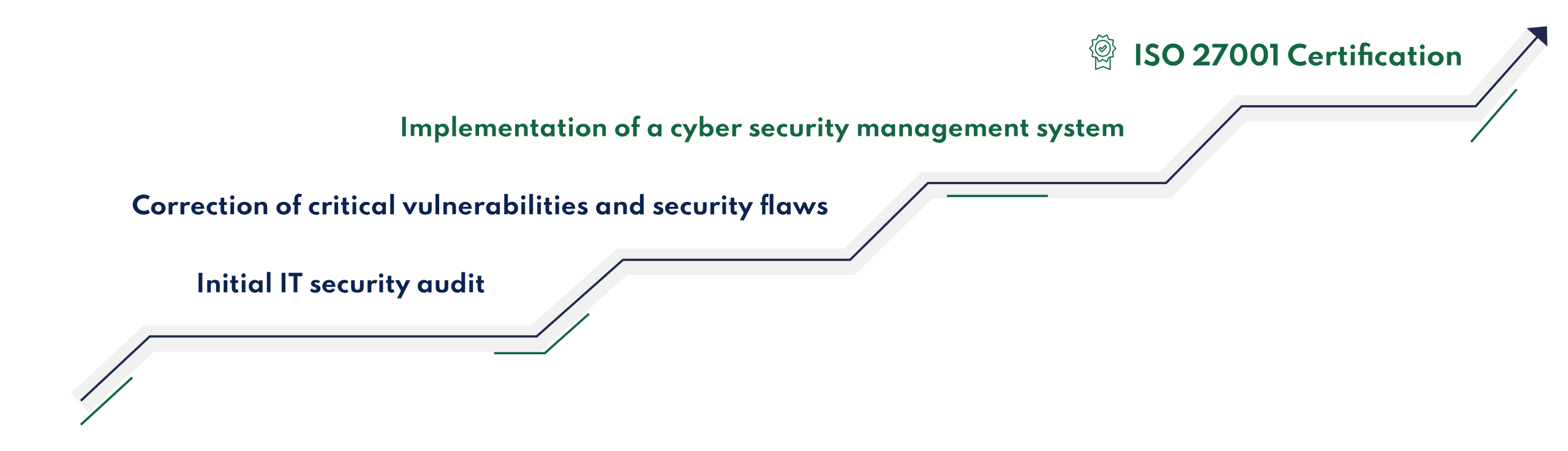
This audit can be integrated into a gap analysis or ISO 27001 internal audit. Following this, our teams will be able to support you throughout the process of obtaining ISO 27001 certification.
Our strengthss
Protection
Data protection and information security are our core business
Certification
We are ourselves an ISO 27001-certified organization.
Expertise
Our certified experts benefit from hands-on experience in entities of all sizes and types
Our team will support you throughout your data security process to help you achieve your compliance and security objectives.





